IAME

Introduction
Current identification systems rely on people having to share their personal information and supporting evidence with counterparties in order to identify themselves and their source of wealth. Those counterparties hold the shared data wholly, and the more data a person shares with those counterparties, the easier it is to identify the person and their source of wealth. If a person is to transact with n counterparties, it results into a topological star network with n nodes, each acting as point of vulnerability to the data sharer. Regardless of security measures, the more data a person surrenders, the more severe the fallout from any potential security breach.
All too often the counterparties/nodes do share the data partially or wholly with third parties, which in turn extends the initial star network, hence increasing the number of points of vulnerability in the former network. Technological innovation in encryption mostly work with regards to securing the transmission of data between two or more nodes in a network, however they do not address the issue of an increase in the number of nodes in a sensible data network. As the number of electronic transactions a person conducts increases in frequency, the number of nodes in their personal data network subsequently increases exponentially, consequently increasing the number of points of vulnerability
Deconstructing the Identification Process
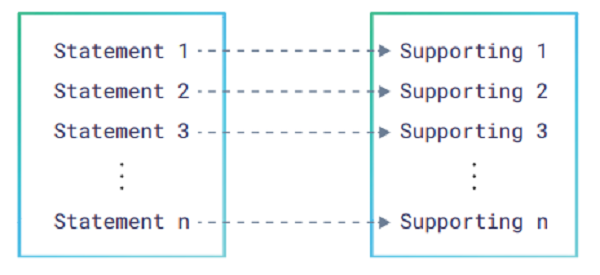
The process assumes that: if the party is genuine then all provided statements can be mapped onto supporting documentation. In principle, the more data that can be mapped on more supporting documents, the more difficult it is for a party to falsify its identity.
The mapping process itself is quite simplistic and can be categorized as follows:
- 1. Statement to string confirmation
2. Statement to non-string confirmation
3. Statement to publicly available information confirmation
4. Statement to privately available information confirmation
5. Statement to government records confirmation.
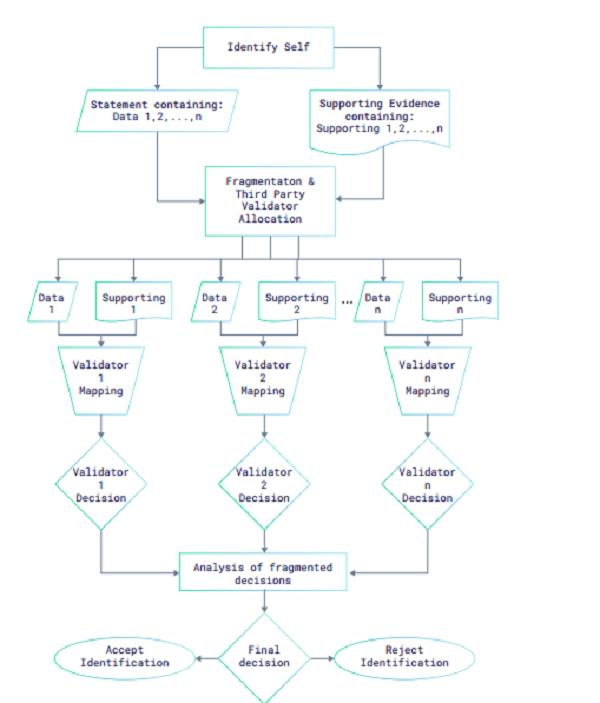
Fragmenting the Identification Process
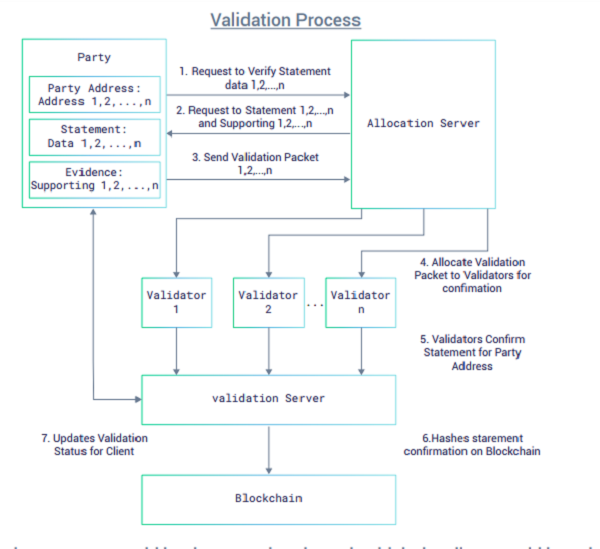
The IAME Identification Network
The IAM Token
The IAM Token
To operate the IAME Identification Network, a functional token will be issued, known as the IAM Token, which would operate as a validation token to initiate confirmation requests for validation packets on the IAME Identification Network. Parties would spend the token through the IAME Identification Network client and after deduction of equivalent blockchain hashing costs, the balance of IAM token would be paid out as reward to third-party validators who operate the validation processes on a for-profit basis.
HELLO GUYS GO JOIN THIS ICO, I BELIEVE, YOU AND ME WILL BE A SUCCESS…!!
WEBSITE : https://iame.io/
WHITEPAPER: https://iame.io/res/180301-IAME-White-Paper-en.pdf
TELEGRAM : https://t.me/IAME_identity
MY BITCOIN USERNAME : Efta321
MY ETH WALLET ADDRESS : 0x8B447B829139f1E2E237fAee31604e60b03bC41E
WHITEPAPER: https://iame.io/res/180301-IAME-White-Paper-en.pdf
TELEGRAM : https://t.me/IAME_identity
MY BITCOIN USERNAME : Efta321
MY ETH WALLET ADDRESS : 0x8B447B829139f1E2E237fAee31604e60b03bC41E
Comments
Post a Comment